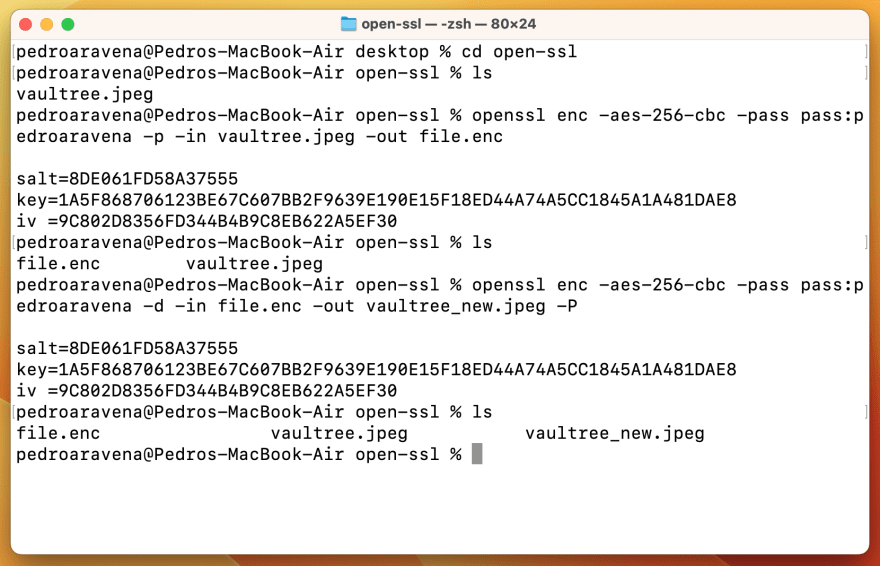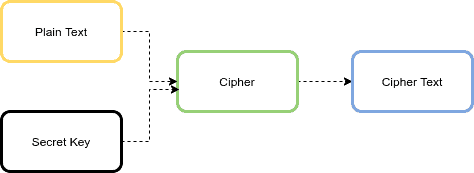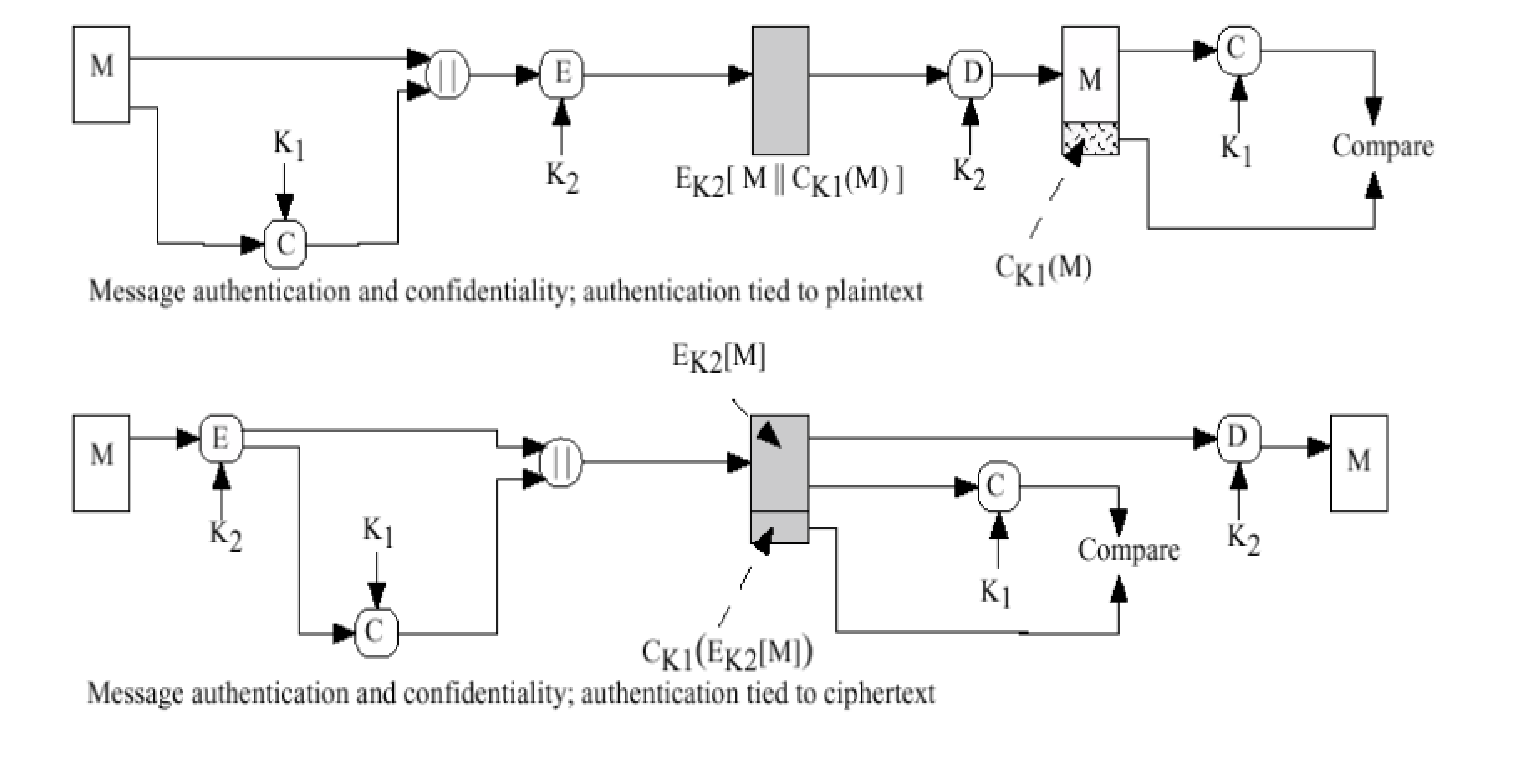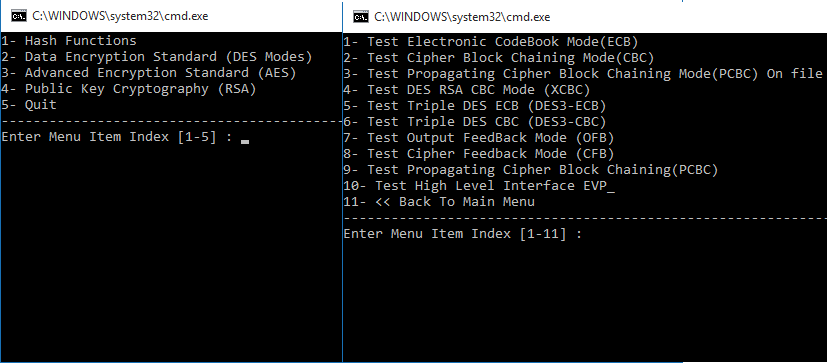
9.8. Encryption — TERASOLUNA Server Framework for Java (5.x) Development Guideline 5.3.1.RELEASE documentation
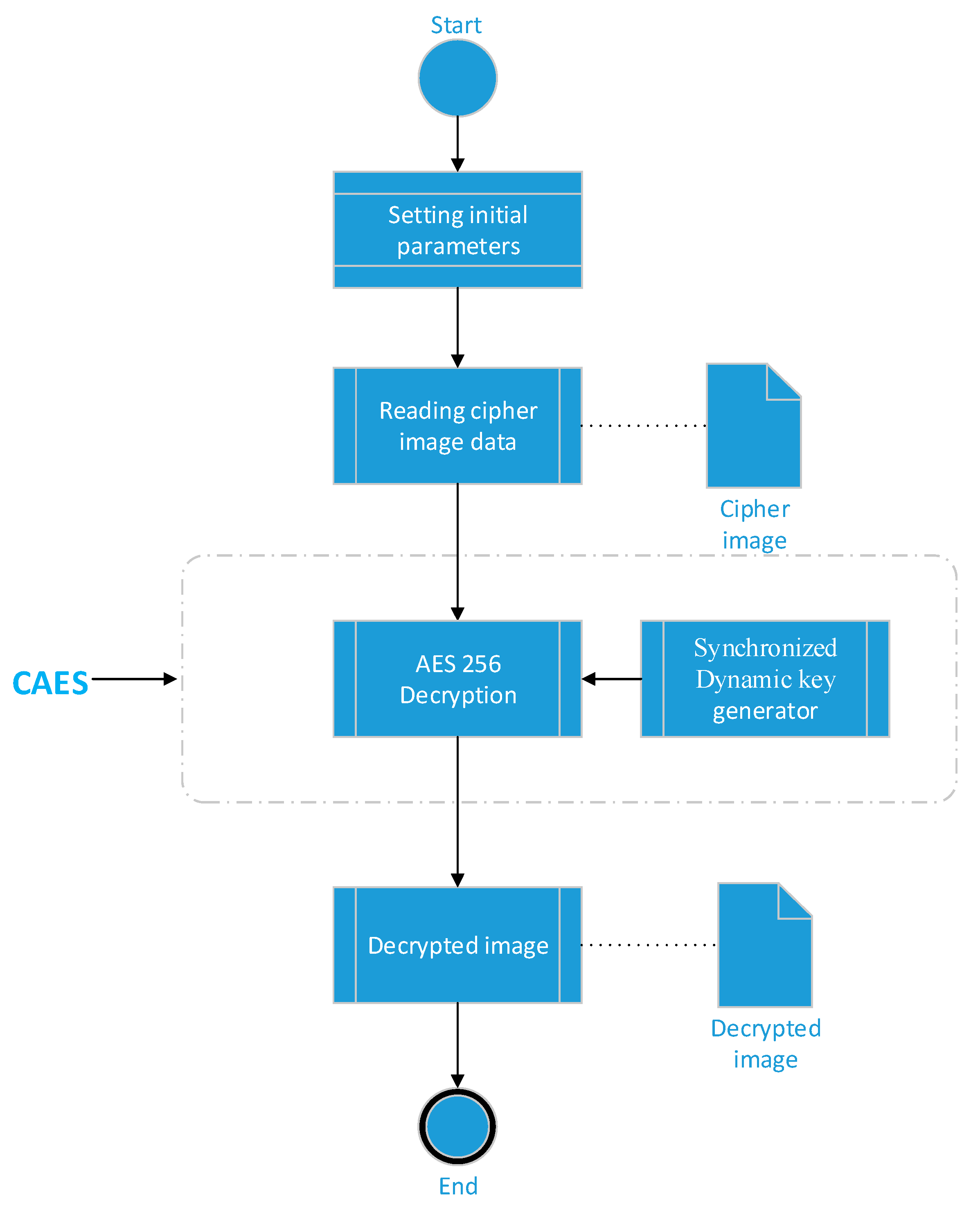
Applied Sciences | Free Full-Text | Chaos-Based Synchronized Dynamic Keys and Their Application to Image Encryption with an Improved AES Algorithm